Difference between revisions of "VPN"
(Created page with "A Virtual Private Network is a way of pretending your computer is connected to a different network. == Concept == File:VPN.png|thumb|1000px|Shematic of a full-tunnel VPN co...") |
m |
||
| (4 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| + | [[Category:Basics]] | ||
A Virtual Private Network is a way of pretending your computer is connected to a different network. | A Virtual Private Network is a way of pretending your computer is connected to a different network. | ||
== Concept == | == Concept == | ||
| − | [[File:VPN.png|thumb|1000px| | + | [[File:VPN.png|thumb|1000px|Schematic of a full-tunnel VPN connection]] |
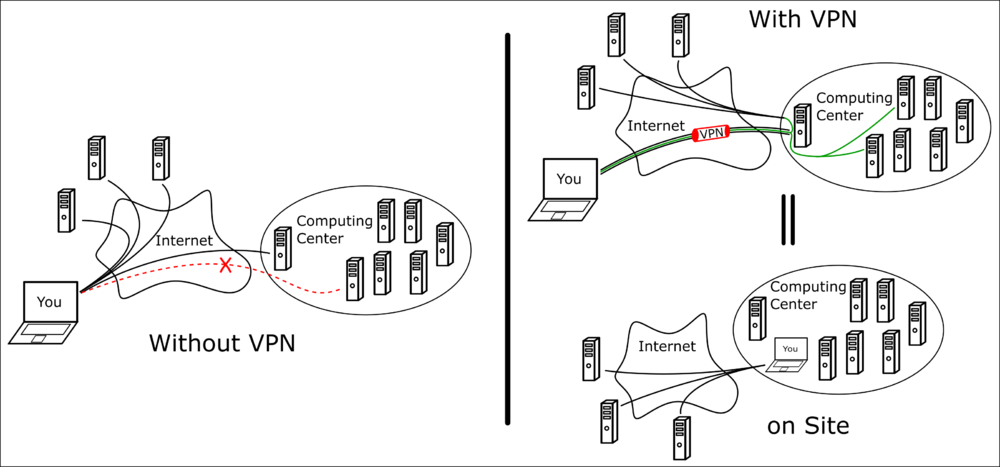
| − | The idea of a VPN connection can be best understood with the given | + | The idea of a VPN connection can be best understood with the given schematic: |
| − | On the left side is the classical | + | On the left side is the classical scheme of contacting other computers/servers/websites directly through your internet connection. |
| − | On the right hand side, a VPN is employed | + | On the right hand side, a VPN is employed. A VPN is one connection/tunnel, through which all your connections are routed. Your computer is only connected to the computing center, but for every other computer it looks like it is physically plugged into the computing center. The tunnel, where your information is routed through is usually secured and encrypted. |
== Advantages == | == Advantages == | ||
| Line 15: | Line 16: | ||
As well as: | As well as: | ||
| − | * For every other entity | + | * For every other entity on the internet your connection seems to be coming from the computing center, which might be helpful for e.g. accessing library articles or materials restricted to the computing center. |
| − | * Your whole connection is encrypted up to the computing center | + | * Your whole connection is encrypted up to the computing center. As an effect your internet provider or for example Starbucks, whose Wifi you might be using, gets no information what you are doing with the internet connection and just sees an encrypted tunnel. Instead only the computing center has this information. |
== How-to-Use == | == How-to-Use == | ||
Depending on your computing center the usage of VPN unfortunately differs. Cisco AnyConnect Secure Mobility Client is a widely used software, but information on how to download and configure this, can only be found on the [[Site-specific documentation|Site-specific documentation]] of your local computing center. | Depending on your computing center the usage of VPN unfortunately differs. Cisco AnyConnect Secure Mobility Client is a widely used software, but information on how to download and configure this, can only be found on the [[Site-specific documentation|Site-specific documentation]] of your local computing center. | ||
Latest revision as of 09:23, 5 September 2019
A Virtual Private Network is a way of pretending your computer is connected to a different network.
Concept
The idea of a VPN connection can be best understood with the given schematic:
On the left side is the classical scheme of contacting other computers/servers/websites directly through your internet connection.
On the right hand side, a VPN is employed. A VPN is one connection/tunnel, through which all your connections are routed. Your computer is only connected to the computing center, but for every other computer it looks like it is physically plugged into the computing center. The tunnel, where your information is routed through is usually secured and encrypted.
Advantages
This technique has a couple of advantages:
- For everybody inside the computing center your computer seems to be sitting right there, allowing you to access internal information and opening connections that might not be allowed from an external address (depicted in red on the left side).
As well as:
- For every other entity on the internet your connection seems to be coming from the computing center, which might be helpful for e.g. accessing library articles or materials restricted to the computing center.
- Your whole connection is encrypted up to the computing center. As an effect your internet provider or for example Starbucks, whose Wifi you might be using, gets no information what you are doing with the internet connection and just sees an encrypted tunnel. Instead only the computing center has this information.
How-to-Use
Depending on your computing center the usage of VPN unfortunately differs. Cisco AnyConnect Secure Mobility Client is a widely used software, but information on how to download and configure this, can only be found on the Site-specific documentation of your local computing center.